Live Feed
Today, February 22, 2026
07:57
Whale Alert reported that 700,000,001 USDT has been transferred from HTX to Aave. The transaction is valued at about $700 million.
Yesterday, February 21, 2026
15:01
We provide real-time cryptocurrency updates around the clock from 10:00 p.m. UTC on Sunday through 3:00 p.m. UTC on Saturday. Outside these hours, coverage is limited to critical market-moving developments.
14:10
Private equity and private credit manager Blue Owl Capital is selling $1.4 billion in assets to meet redemptions, sparking speculation that the event could trigger the next Bitcoin bull run, CoinDesk reported. Following the announcement, Blue Owl's (OWL) stock has fallen approximately 14% on the week and is down more than 50% for the year.
Former PIMCO CEO Mohamed El-Erian warned the situation could be a "canary in the coal mine," similar to the 2007 collapse of Bear Stearns. The speculation is rooted in historical precedent: the Federal Reserve's zero-interest-rate policy and quantitative easing (QE) following the 2008 financial crisis set the stage for Bitcoin's creation and subsequent long-term bull market. Similarly, after massive liquidity injections during the 2020 COVID-19 crisis, BTC surged from under $4,000 to over $65,000.
14:04
Searches for the phrase "Bitcoin is dead" have hit an all-time high on Google Trends, U.Today reported. According to on-chain platform Solid Intel, the spike in searches occurred as BTC was trading near the $68,000 level. This pattern is considered a classic signal of market fear during sharp downturns and has historically coincided with major market bottoms.
13:39
Robert Kiyosaki, author of 'Rich Dad Poor Dad,' has purchased an additional Bitcoin (BTC) for $67,000, CryptoPotato reported. Kiyosaki explained on X that he anticipates the U.S. Federal Reserve will resort to massive currency printing when the dollar's value collapses due to the national debt crisis. He also argued that as the mining of the 21 millionth Bitcoin draws nearer, BTC will become superior to gold once its total supply is reached. However, due to Bitcoin's halving mechanism, the final BTC is not expected to be mined until around 2140.
13:33
The Indian government is reviewing the impact of the U.S. Supreme Court's ruling on President Trump's tariffs, Walter Bloomberg reported via X. He added that the French government has stated that the European Union (EU) has the tools to respond to President Trump's tariff measures.
12:48
Cryptocurrency exchange Bitfinex has stated that quantum computing has not yet reached a stage where it can threaten Bitcoin's (BTC) cryptographic systems, according to U.Today. In a post on X, Bitfinex explained that breaking Bitcoin's encryption would require millions of stable qubits and the ability to run "Shor's algorithm" on a large scale, a level far beyond current capabilities. The exchange also noted that community-level discussions on countermeasures are underway, including transitioning to wallet structures that minimize public key exposure, introducing lattice-based signatures, and the BIP-360 proposal. Bitfinex added that if the quantum threat does materialize, it is most likely to do so after the mid-to-late 2030s.
12:18
With Bitcoin down around 50% from its high last October, the monetary policy direction of U.S. Federal Reserve Chair nominee Kevin Warsh is emerging as a key market variable, DL News reported. The market perceives Warsh as a hawk, raising concerns that he may slow the pace of interest rate cuts and potentially shrink the Fed's balance sheet. Pepperstone analyst Dylin Woo stated that if Warsh pursues aggressive monetary tightening, volatility in the cryptocurrency market is likely to increase. Similarly, Axis co-founder Jimmy Shieh analyzed that the 14% drop in BTC immediately following the nomination reflects concerns over Warsh's hawkish monetary philosophy. However, some experts suggest that Warsh's long-term positive view of Bitcoin as a store of value could strengthen the narrative of the asset as a hedge against Fed policy risks.
11:26
A whale dormant for five years has deposited 1,000 BTC, worth approximately $67.64 million, to Bitfinex, Onchain Lens reported. The whale had previously withdrawn the BTC from Bitstamp and FTX. At current prices, the position represents an unrealized profit of about $38.35 million.
11:08
The IoTeX (IOTX) bridge has been exploited due to a private key leak, resulting in the theft of $8 million worth of cryptocurrency, according to a report from PeckShield. The security firm noted that the stolen funds were first swapped for Ethereum (ETH) and are now being bridged to Bitcoin (BTC) through ThorChain. PeckShield added that the attacker appears to be in the process of laundering the funds.
11:01
South Korean crypto exchanges Upbit, Bithumb, and Coinone have announced the temporary suspension of IoTeX (IOTX) deposits and withdrawals. The move follows a potential security incident involving the project, and services will remain halted until the stability of deposits and withdrawals can be confirmed.
09:59
Whale Alert reported that 200,000,000 USDT has been transferred from an unknown wallet to Binance. The transaction is valued at about $200 million.
09:26
Whale Alert reported that 200,000,000 USDT has been transferred from an unknown wallet to Binance. The transaction is valued at about $200 million.
08:52
Whale Alert reported that 800,000,000 USDT has been transferred from Binance to an unknown wallet. The transaction is valued at about $800 million.
08:48
BTC perp long/short ratios on top exchanges by open interest
The following are the 24-hour long/short ratios for BTC perpetual futures on the world’s three largest crypto futures exchanges by open interest:
Overall: 49.67% long, 50.33% short
- Binance: 49.93% long, 50.07% short
- OKX: 49.07% long, 50.93% short
- Bybit: 48.98% long, 51.02% short
07:03
BTC mining firm MARA Holdings (MARA), formerly Marathon Digital, has acquired a 64% stake in Exaion, a subsidiary of French power company EDF, Cointelegraph reported. The acquisition is part of a strategy to expand its artificial intelligence and cloud services businesses, MARA Holdings explained.
06:32
Japanese financial giant SBI Holdings has launched an on-chain bond that pays investors in XRP, The Crypto Basic reported. The bond, issued and managed on a blockchain, is worth a total of 10 billion yen (approximately $64.5 million) and targets individual investors. Investors will receive XRP corresponding to their investment amount immediately after subscribing and can receive additional XRP rewards when interest is paid one to three years later.
05:59
U.S. Ethereum spot ETFs saw a net outflow of $670,000 on Feb. 20, marking their third consecutive day of net outflows, according to Trader T.
- BlackRock's ETHA: +$1.78 million
- Fidelity's FETH: -$2.45 million
05:56
U.S. spot Bitcoin ETFs recorded a total net inflow of $88.05 million on Feb. 20, according to data compiled by Trader T. The inflow reverses a three-day streak of net outflows.
- BlackRock's IBIT: +$64.46 million
- Fidelity's FBTC: +$23.59 million
05:22
Although retail investors are buying Bitcoin, an analysis suggests that participation from whale investors is necessary for a meaningful rally. CoinDesk reported that, according to data from Santiment, holdings in wallets with less than 0.1 BTC—typically associated with retail investors—have increased by 2.5% since Bitcoin hit its all-time high last October. This growth has brought their share of the total supply to its highest level since mid-2024. In contrast, the supply share held by whale wallets, defined as those holding between 10 and 10,000 BTC, has decreased by approximately 0.8%. The report concludes that demand from retail investors alone is insufficient to sustain an uptrend, leading to unstable and volatile price movements, and that a shift to net buying by large-scale investors is now required.
05:03
The following shows estimated liquidation volumes and position ratios for major crypto perpetual futures over the past 24 hours:
- BTC: $69.69 million liquidated (64.74% shorts)
- ETH: $33.03 million liquidated (54.51% shorts)
- SOL: $8.08 million liquidated (72.15% shorts)
03:56
Whale Alert reported that 200,000,000 USDT has been transferred from an unknown wallet to Binance. The transaction is valued at about $200 million.
03:03
Tether, the issuer of the world's largest stablecoin USDT, has announced it will discontinue support for its offshore yuan-pegged stablecoin, CNH₮. Support and new token issuance will cease immediately. The company attributed the decision to market conditions and limited demand, adding that the scale of CNH₮ was insufficient to justify continued operational support. Redemptions will remain available for one year following the announcement. Tether first launched support for the stablecoin in December 2022.
01:29
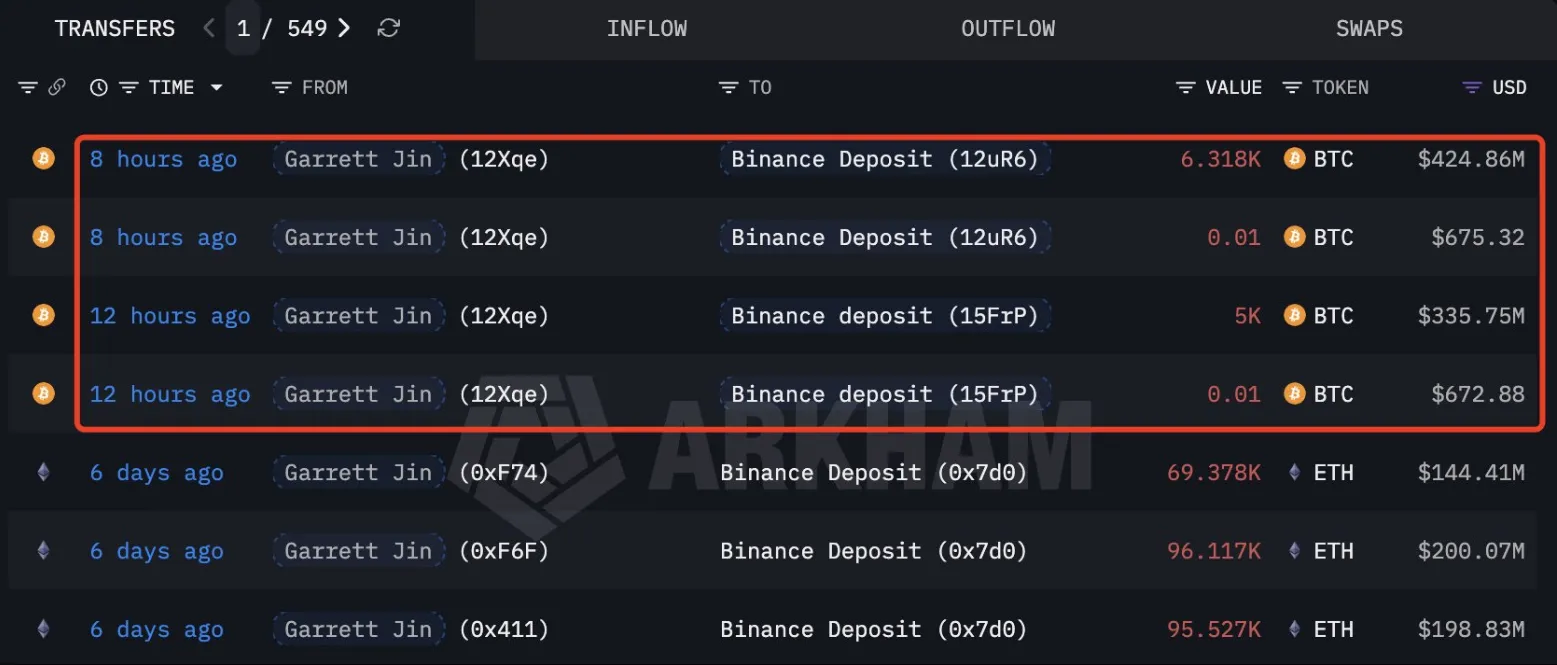
An address presumed to belong to BitForex founder Garrett Jin has deposited an additional 6,318 BTC, worth $424.86 million, to Binance, Lookonchain reported. This follows a previous deposit of 5,000 BTC from the same address.
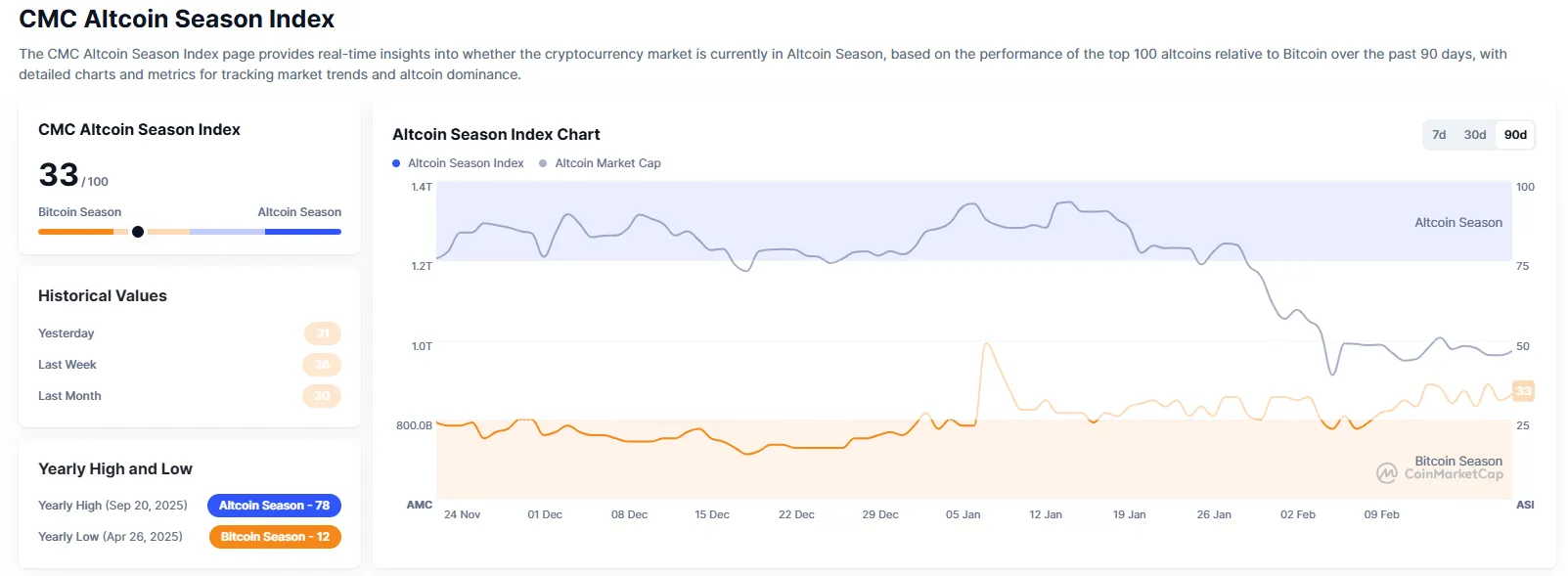
00:56
The Altcoin Season Index from crypto data aggregator CoinMarketCap has dropped two points from yesterday to 33. The index measures market sentiment by comparing the performance of the top 100 cryptocurrencies by market capitalization, excluding stablecoins and wrapped tokens, against Bitcoin over the past 90 days. An 'altcoin season' is declared when 75% of these top altcoins outperform Bitcoin during that period. A score closer to 100 indicates a stronger altcoin season.